Business IT, Remote Access, Security
Working From Home – Allow Your Staff to Work From Home Securely
As a result of the COVID-19 outbreak, everyone’s suddenly talking about working from home, but many smaller businesses don’t have the facilities or policies for this already set up. It’s important that businesses take an intelligent, considered approach to this and don’t just give their staff unfettered access to the work network – cyber criminals are watching closely to take advantage of businesses allowing remote access haphazardly, so those that aren’t careful could go from a remote workforce business to no business in short order.
Fortunately, it isn’t particularly difficult to provide staff secure access to all the facilities they would usually use at work – indeed, they can use exactly the same systems using remote access, and this is probably the best way to do it. You see, if they remotely access their own work PCs from home, they have access to all their emails, bookmarks, applications and business files without having to set anything up on their home computer. That also means the files they’re working on will never leave your office – with remote access, the user is just looking at a remote monitor session of what’s happening on the work PC, the files are still being worked on from the office PC and they never leave the work network.
To enable such operation, users need to be given remote access user rights, and the functionality needs to be enabled on the PC. It’s best to do this from Group Policy if your computers are part of a Microsoft Domain with Active Directory, but it can be enabled by hand on individual PCs if not.
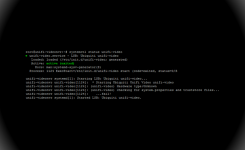
But how do staff actually connect to the work network? It isn’t a great idea to open up your firewall to allow dozens of remote desktop sessions to individual PCs (while Microsoft RDP is an entirely secure protocol, that doesn’t mean a vulnerability won’t be found at some point in the future, and it’s a potential attack vector, so opening up all those ports is just asking for trouble). To do this properly, you should have a VPN server provide remote network access to your staff, which is a secure, encrypted connection and makes it look like their remote computer is connected directly into your local work network. They can then use RDP (Remote Desktop Protocol) to get direct access to their specific PC and operate as normal from there.
If you don’t have a VPN server, it isn’t particularly difficult, time consuming, nor expensive to set up. However, it’s important to ensure that it’s done properly – you should only be using SSTP, IKEv2 or OpenVPN. Absolutely do not use PPTP – if you have an existing VPN that uses PPTP, you should be decommissioning it and shifting to something that actually provides security. Some organisations also have hardware routers that allow for external VPN connections, however given the severity of recent vulnerabilities discovered in some of the most expensive routers designed for corporate and government networks, my recommendation would be for SMBs to steer clear of hardware based VPN solutions unless you have dedicated on-staff network engineers who can manage such devices and ensure they are kept fully patched.
With VPN set up, staff can securely connect to the work network, then work from the very PCs they use on a day-to-day basis. The only thing left to cover is your remote access policy. Yes, you absolutely must have a policy in writing to ensure staff are aware of their obligations accessing the work network from home. This policy needs to stipulate whether or not they can download, copy, or print any work information to their home PCs, devices or printers. The importance of confidentiality, privacy and security must be stressed – if staff aren’t meant to take documents out of the office, then they shouldn’t be taking copies of anything outside their RDP session on their work PC. No, it isn’t a technical measure that can prohibit such behaviour, but it will ensure that staff are fully aware of their obligations and will curb anything but those deliberately intent on exfiltrating data.
There are technical measures you can put in place that can track and limit data movement, but such features, software and technology are generally beyond the budgets of smaller businesses. If you don’t have such infrastructure set up to control employee behaviour inside your office there’s nothing stopping them taking data out while they’re there, anyway. A well worded policy guides employee behaviour and provides you with a strong legal basis for enforcement should it be required.
Of course, if you have cloud-based infrastructure such as GSuite or Microsoft 365, your staff can work from anywhere already, and you’ve probably already got a good data access policy in place. But for those currently relying on on-premises infrastructure, I’d recommend against jumping ship to the cloud as a knee-jerk reaction – such changes need to be planned and managed properly, and while the current situation may well warrant conversations and consideration of alternative infrastructure, don’t start from the position of the decision having already been made and trying to shoehorn a solution in to rapidly solve this problem for you, as it will cause you more problems than you started with.
Finally, there are of course other considerations such as equipment (whether staff have a workspace and device to connect from home) and insurance (staff should be covered by standard workers compensation provisions when working from home), so you need to ensure you understand these requirements and obligations as an employer.
If you’re interested in setting up remote access facilities for your business and you don’t know where to start, please feel free to get in touch.